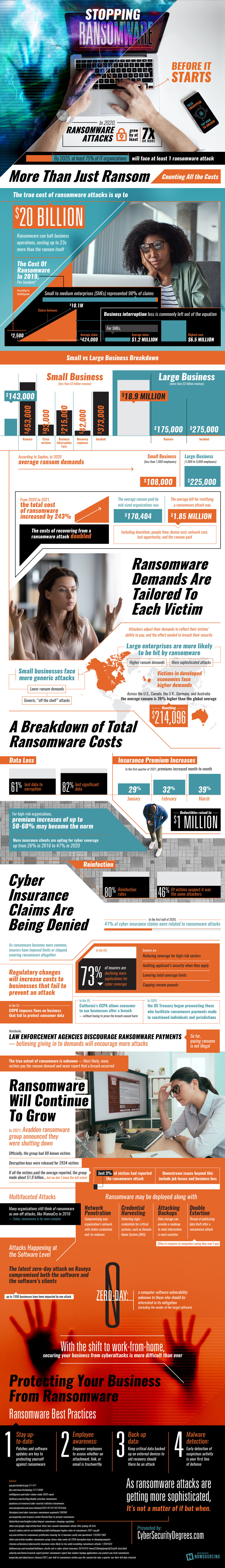
How to Stop Ransomware Before it Starts
In 2020, ransomware attacks grew by at least 7x. In 5 years, at least 75% of IT organizations will face a ransomware attack at least once. The true cost of ransomware attacks is up to $20 billion. This dollar value isn’t just ransom payments: ransomware can halt business operations, costing up to 23x more than the ransome itself. In 2019, the average claim for small and medium businesses was $424,000. The average ransom demand accounts for only $108,000 of that amount. Other damages include crisis services, loss from business interruption, and recovery expenses.
An important thing to remember about ransomware attacks is that they are personalized. Attackers adjust their demands to reflect their victims’ ability to pay and the effort needed to breach their security. Victims from developed economies like the US, Canada, the UK, Germany, and Australia face a 26% higher ransom than the global average. Large businesses are more likely to face high ransom demands from sophisticated attacks. Smaller businesses, on the other hand, are more likely to fend off generic, “off the shelf” attacks. Despite the relatively weaker threat, small businesses are still vulnerable because their cybersecurity system tends not to be as robust.
Perhaps the most concerning aspect of ransomware is the potential for reinfection. As difficult as it is to recover from one ransomware attack, no business wants to be victimized again. Yet reinfection rates are up to 80%. 46% of repeat victims suspect the same attackers targeted them multiple times.
Is insurance a solution to financial recovery? Not necessarily. Cyber insurance claims are being denied. As ransomware becomes more common, insurers have imposed limits or stopped covering ransomware altogether. In the US, 73% of insurers are declining more applications for cyber coverage. High risk sectors and applicants with weak security are less likely to be approved for insurance. For those with coverage, total coverage limits are falling and ransom payments are being capped. Meanwhile, premium costs are rising. Premiums of up to 60% may become the norm going forward.
Regulatory changes are creating an environment hostile to businesses that fail to prevent an attack. In the EU, the GDPR imposes fines on businesses that fail to protect consumer data. In the US, California’s CCPA allows consumers to sue businesses after a breach without needing to prove the breach caused them harm. Last year, the US Treasury also began prosecuting those who facilitate ransomware payments to sanctioned individuals and jurisdictions. So far, the act of paying ransom itself is not illegal, though law enforcement agencies discourage the practice.
Given these dangers, what can businesses do to stay safe? Here are a few tips. Stay up to date on patches and software updates. Make sure employees know whether an attachment, link, or email is trustworthy. Keep critical data backed up on external devices to aid recovery should an attack occur. Finally, make sure malware detection software is in use: early detection is the first line of defense. Ransomware attacks are not ifs, but whens.